Cryptocurrency Storage: Security vs. Convenience
Explore the best cryptocurrency storage options, including software wallets, hardware wallets, and multisig solutions. Learn the importance of self-custody and the risks of relying solely on exchanges for your crypto assets.
USER GUIDES
2/3/20256 min read


When Getting Into Crypto The Amount of Wallets Can Seem Overwhelming
The cryptocurrency revolution empowers individuals with unprecedented control over their finances. 1 However, with this power comes responsibility. This article explores the concept of self-custody, empowering you to take control of your cryptocurrencies and safeguard your digital wealth. In order to store your crypto assets, there are a few options, each with differing levels of convenience and security. The two branches which one can go down is either self custody storage, meaning you control the keys to the assets, this would include software wallets, hardware wallets and paper wallets or non self custody in which the keys would be controlled by an exchange or other platform the assets are stored on. As the renowned bitcoin pioneer and innovator Andreas M Aantonopolous says "Not your keys, not your crypto", meaning if you do not control your own keys personally, then the crypto is not controlled by you. This has been a factor time and time again when crypto exchanges face bankruptcy, corruption issues and irresponsible fund management as we have seen infamously with the Mt GOX exchange as well more recently with FTX, where these issues completely wiped out the funds deposited by some users and others getting a small percentage back, so it is essential that crypto assets are managed appropriately as this is a class of digital asset in which individuals can hold themselves with very limited third party trust. Where would you feel your digital assets are safer?
Empowerment of The Individual Through Digital Currency
With each increase in the level of security of crypto asset storage, there is an added level of responsibility for ones own assets. If the assets are being self managed and the private keys gets lost, then the assets are effectively lost, so it is essential to take precautions and manage these assets with caution, just as on the German Autobahn (highway) system there are sections without speed limits in which the responsibility for maintaining a safe speed is within the driver's control and is not enforced by third parties, empowering the individual
Security Level One - Exchanges including Coinbase, Gemini and Binance
This crypto storage method is the most convenient as the user can be easily "onramped" easily, which is that there is a direct link between the exchange and their banking services so the funds can easily be deposited to purchased the desired crypto assets. The assets can then be stored on the exchange without having to move the funds to a different wallet and do not require the user to manage any keys, just a username and password. This method offers a high level of convenience at the cost of security, in 2022 FTX, a major crypto exchanage which managed approximately 40 billion dollars worth of assets collapsed. This was largely due to irresponsible fund management as they had issued a speculative token and irresponsibly borrowed funds for future expansion against their volatile FTT token. When that token crashed as many cryptocurrencies do, it accelerated the downfall of the exchange, with users only receiving a portion back of their deposited assets after the exchange's eventual demise. Often the convenience factor is not worth the potential risk and it may be better for some crypto holders depending on their situation to move up the security ladder to more secure options for this asset class
Security Level Two - Software Wallets
Software wallets maintain a level of convenience while allowing the user to manage their own private keys. This is done by securely storing the private key on the device in which the wallet is being accessed (phone or laptop). This method involves a higher level of responsibility as now the cryptographic keys need to be managed by the user. Many of the risk factors of storing the assets on an exchange are now eliminated, but new factors emerge with this setup. One being the mismanagement of the key, which could be potentially lost due to a reboot of the hardware and if user has not made a key backup, the funds could be lost. Storing the key on a cloud service which would also be irresponsible as it could be compromised. A vector for attack would be the device you are using the software wallet on being hacked, thus exposing the private key and potentially draining your crypto assets. With all of these new ways in which the funds could be compromised, software wallets are great to use if you value convenience and control of your own assets without too much further hassle. Software wallets such as Phantom and Metamask are great for direct DEFI interactions, but more caution must be taken if storing a larger amount of crypto assets for the long term
Security Level Three - Hardware Wallets
Hardware wallets offer a higher level of security compared to software wallets. Unlike software wallets, where the private keys are stored on the user's device (which can be vulnerable to malware and hacking), hardware wallets store the private keys securely within a dedicated device.
To make a transaction, the hardware wallet generates a digital signature, proving ownership of the funds without ever exposing the private key to the internet. This requires physical interaction with the device, typically by connecting it to a computer or mobile device. While this adds a layer of convenience compared to software wallets, it enhances security significantly.
Furthermore, most hardware wallets incorporate a secure element chip, a tamper-resistant component that protects the private key from unauthorized access, even if the device itself is compromised.
This robust security makes hardware wallets ideal for long-term storage and holding significant amounts of cryptocurrency. However, the added security comes at the cost of convenience. The need to physically interact with the device can make frequent transactions more cumbersome, making them less suitable for frequent trading or interacting with decentralized applications
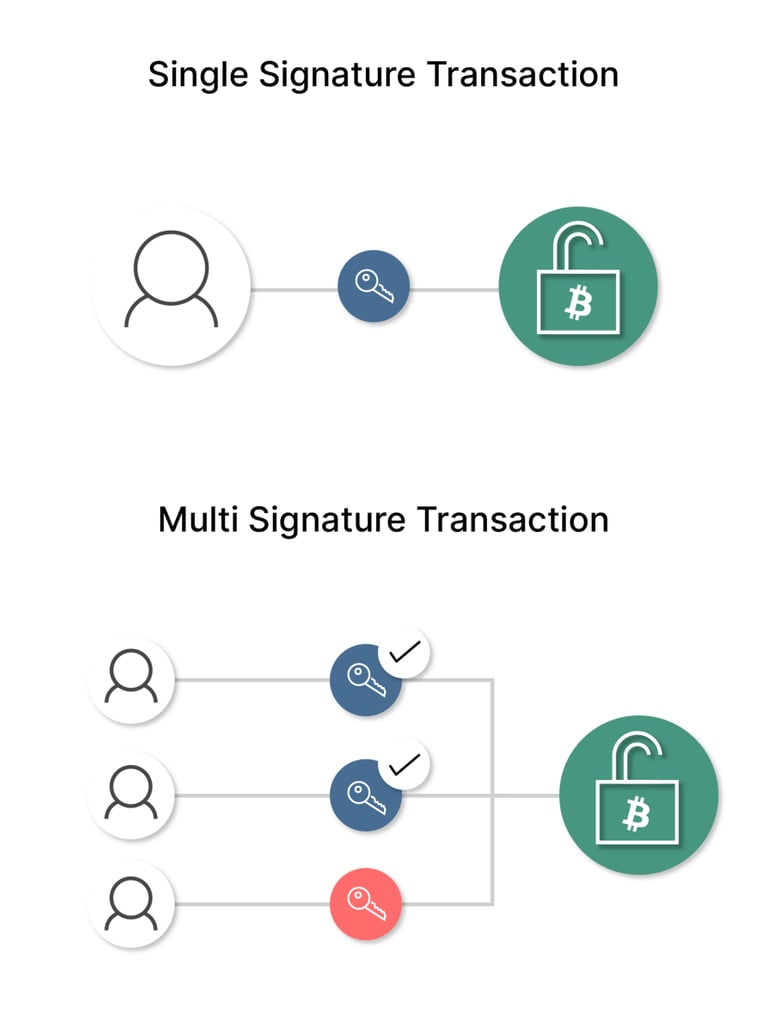
Level 4 - Multisig wallets
Multisig, short for "multi-signature," is a security mechanism that enhances the safety of cryptocurrency transactions. It operates by requiring multiple private keys to authorize the movement of funds. This collaborative approach distributes control among several individuals or entities, creating a more secure and robust system.
At the core of multisig lies a defined threshold: the minimum number of signatures necessary to approve a transaction. Each authorized party possesses a unique private key. To execute a transaction, the required number of key holders must provide their signatures. This multi-layered approval process significantly increases the security of cryptocurrency holdings.
Ideal Use Cases for Multisig
Corporations and Businesses: Multisig provides a robust framework for managing corporate cryptocurrency assets. It enhances security by preventing unauthorized transactions, promotes sound governance through collective decision-making, and ensures business continuity in the event of key personnel unavailability.
Decentralized Autonomous Organizations (DAOs): In the context of DAOs, multisig facilitates community governance and ensures that funds are utilized according to community-approved proposals. This fosters transparency and accountability within decentralized organizations.
High-Value Asset Management: For individuals and entities holding significant cryptocurrency assets, multisig offers an additional layer of protection. By requiring multiple approvals for any transaction, it significantly reduces the risk of unauthorized access and theft
While multisig offers unparalleled security, it does introduce a degree of complexity. The requirement for multiple signatures can potentially slow down the transaction process. Furthermore, the secure management and distribution of multiple keys can add an administrative overhead. However, for entities prioritizing security and collective decision-making, the enhanced protection offered by multisig often outweighs these minor inconveniences
Type Suited to The User
The choice of cryptocurrency storage method hinges on a delicate balance between convenience and security. Exchanges offer unparalleled ease of use but sacrifice significant control. Software wallets provide a balance of convenience and user control, albeit with increased responsibility for key management. Hardware wallets prioritize security by isolating private keys within a dedicated device, though this comes at the cost of reduced accessibility. Multisig wallets offer the highest level of security through collaborative authorization, making them ideal for high-value assets and organizations. Ultimately, the optimal storage solution depends on individual risk tolerance, the volume of assets held, and the frequency of transactions. By carefully evaluating these factors and selecting the appropriate storage method, individuals can effectively safeguard their digital wealth and navigate the evolving cryptocurrency landscape with confidence


German Autobahn sign - no speed limits








Get in Touch
We'd love to hear from you! Reach out for questions, feedback or other enquiries
Reach
info@bitesizedblockchain.com
Bite Sized is not affiliated with these brands in any way





Grab your daily web 3 byte
